BIC Process Design
Understand & Transform
Supercharge your business operations with the most intuitive AI-powered BPM software.
It seems that you come from a German speaking country. Here you can change the language
English

PLAN
DO


CHECK
ACT


Curious about the value our software can bring to your organization? Our experts will provide a personalized walkthrough, showcasing how our solutions empower over 2,000 customers to achieve their transformation goals and peak performance. See it live in action and discover its impact firsthand!
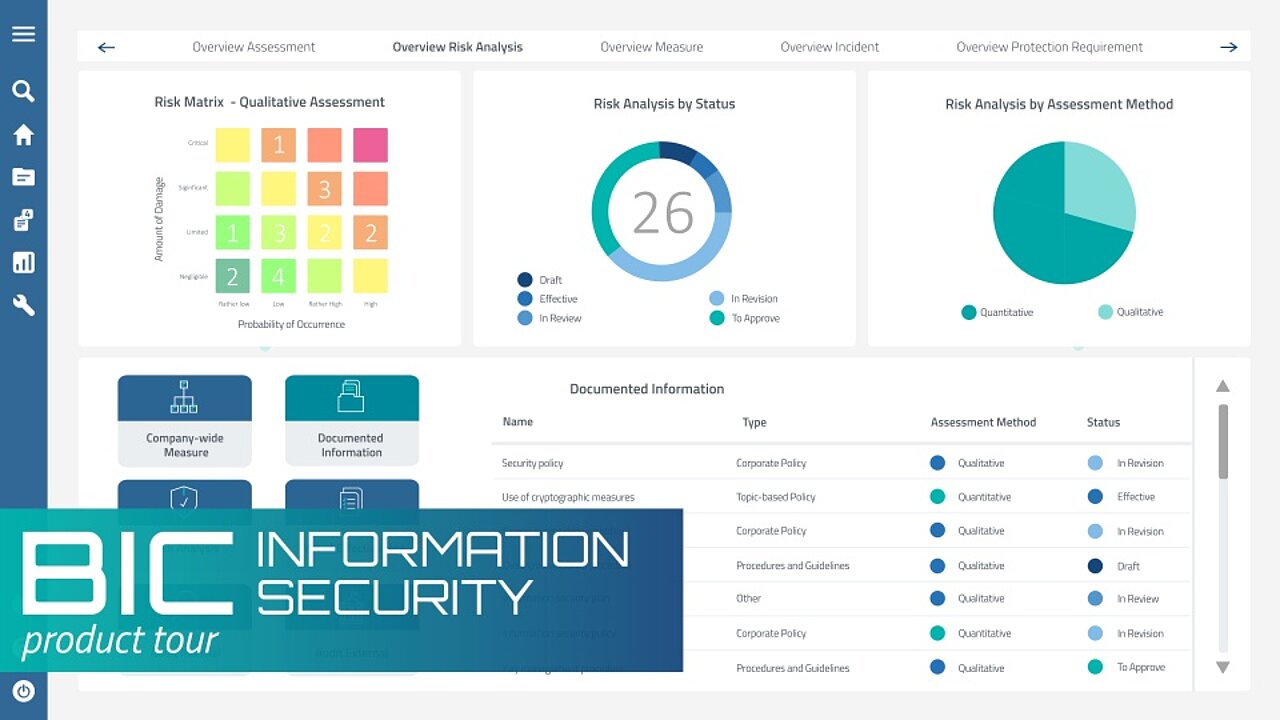
Information security management ensures that sensitive data is kept safe around the clock. By following standardized ISM guidelines and best practices, you can streamline processes and easily meet industry standards such as ISO/IEC 27001 and GDPR. This boosts overall security measures and effectively mitigates information security risks. Read on to find out more about information security management and how to build a solid ISMS framework for your organization.

Lay the groundwork for a robust information security management system with BIC Information Security. Reliably protect your company's assets and ensure sustained business success.

Guarantee comprehensive and streamlined safeguarding for all company assets.

Manage your information security in alignment with the globally recognized ISO Standard 27001.

Save time with automated ISMS processes and bypass the use of Excel applications.

Benefit from pre-defined reports as well as readily available risk and control catalogs.

Access all documented information on your central dashboard.

Utilize ready-made workflows for swift and effective corrective actions whenever necessary.
Want to experience the full power of our tool firsthand? Request a personalized demo now and let our experts guide you through the features and capabilities of BIC Information Security.





